Effective cybersecurity is impossible if you’re only
observing North-South traffic.
Attackers have many ways to bypass perimeter security. Once this happens, effective security depends on organizations having visibility into their internal – East-West or lateral – traffic to detect malware hidden in blind spots or attackers that are attempting to navigate the network.
Threat actors can take weeks or months to traverse the network to locate and exfiltrate high-value data. Gigamon provides complete visibility into all traffic across your network including East-West, encrypted, and container traffic.
Port Spoofing
Visibility into VMs and Containers
Visibility into Apps
Identify threat actors going undetected over non-standard ports.
Eliminate blind spots in the network.
Visualize and manage all application traffic on your network.
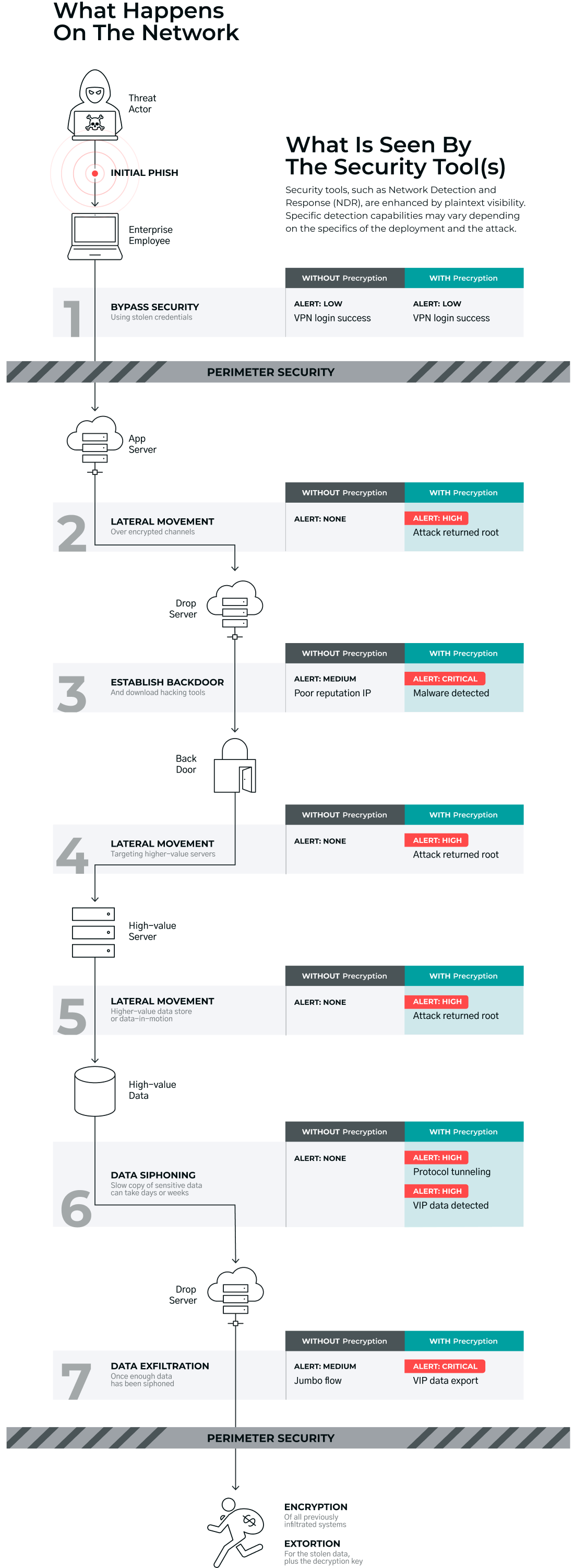
Using Gigamon Precryption™️ Technology to Detect Cybercrime
As threat actors gain sophistication in their ability to perpetrate cybercrime and ransomware attacks, deep observability is critical
for threat detection inside hybrid cloud infrastructure, especially for lateral movement over encrypted channels. Here we contrast the differences in potential threat detection with and without plaintext visibility from Precryption.